How Secure is Apple Keychain? | Apple Password Manager Explained
Discover how secure Apple Keychain really is. Learn about its encryption, safety features, and whether it's the right password manager for you.
Introduction: Why Password Security Matters in 2025???
In a scenario where data breaches, phishing attacks, and password leaks are increasingly common, protecting our personal information has never been more important. With dozens of online accounts to manage, many users rely on password managers to keep their credentials safe and accessible.
Apple offers its own built-in solution called “Apple Keychain.” It’s free, widely available on Apple devices, and often overlooked compared to standalone password managers. But is Apple Keychain really secure? Should you trust it with your most sensitive data? In this blog, we will explore how Apple Keychain works, its security features, its strengths and limitations, and how it stacks up against other password managers.
What is Apple Keychain?
Apple Keychain is Apple's native password management system, pre-installed on all iPhones, iPads, and Macs. It securely stores
Website and app passwords
Credit card information
Wi-Fi network credentials
Secure notes.
Apple Keychain is secure and deeply integrated into Apple's ecosystem, providing automatic syncing across all your devices using iCloud Keychain. It simplifies the login process by automatically filling in credentials securely with just Face ID, Touch ID, or your device's passcode, making it more secure than Android.
How Does Apple Keychain Work?
Apple Keychain stores data locally on the mobile device using strong encryption. When a user enables iCloud Keychain, passwords are securely synced across all of their Apple devices using end-to-end encryption. This means
only the user can decrypt the data
Even Apple can access the stored passwords.
When a user visits a website or logs into an app, Keychain auto-fills the user’s saved credentials after you authenticate with Face ID, Touch ID, or your device’s passcode. Keychain also automatically generates strong, unique passwords for the user when creating new accounts, which helps prevent password reuse, one of the most common security risks. This feature makes it more reliable among other smartphone systems.
Security Features of Apple Keychain
🔐 End-to-End Encryption: Apple Keychain data is protected with 256-bit AES encryption, one of the strongest encryption standards available. Apple never holds user encryption keys, ensuring that even they cannot decrypt user's passwords.
🔑 Two-Factor Authentication (2FA): Accessing iCloud Keychain requires user's Apple ID and 2FA verification, adding an essential layer of security.
🛡️ Device Authentication: Each time apple user use Keychain, it requires authentication via: Face ID Touch ID Device passcode This helps protect user's data if user device is lost or stolen.
🗝️ Password Generator: Apple Keychain suggests complex, unique passwords when creating new accounts to strengthen your online security.
🚨 Password Breach Alerts: Apple notifies user if any of user saved passwords have been involved in known data breaches, allowing user to take immediate action.


How Really Apple Keychain Secure is?
Encryption Strength Apple uses 256-bit AES encryption with a zero-knowledge architecture, meaning user's passwords are encrypted in such a way that Apple cannot read them. User data is tied to user's Apple ID, secured by 2FA and biometric authentication.
Security Across Devices When syncing via iCloud Keychain, Apple uses end-to-end encryption across all user's devices. If one device is compromised then data on other devices remains secure.
Apple’s Privacy Commitment Apple has a strong track record of privacy-first policies. Unlike some free password managers, Apple Keychain is not ad-supported, and Apple does not monetize your personal data. Bottom line: Apple Keychain is extremely secure for everyday users within the Apple ecosystem.
Pros and Cons of Apple Keychain
✅ Pros:
Free and built-in: No additional subscriptions or downloads needed.
Seamless integration: Works automatically across iPhone, iPad, and Mac.
Strong security: Uses advanced encryption and biometric authentication.
Automatic syncing: Keeps passwords updated across all Apple devices.
❌ Cons:
Apple-only: Cannot be used on Windows, Android, or web browsers outside Safari.
Limited features: No password sharing, no secure file storage, fewer advanced options than competitors.
Less user control: No manual backup or export options beyond the Apple system.
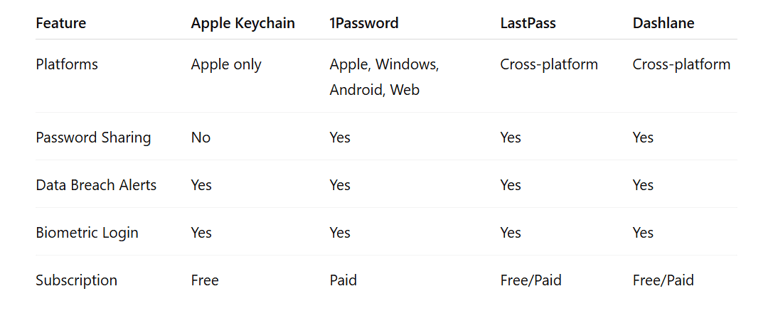
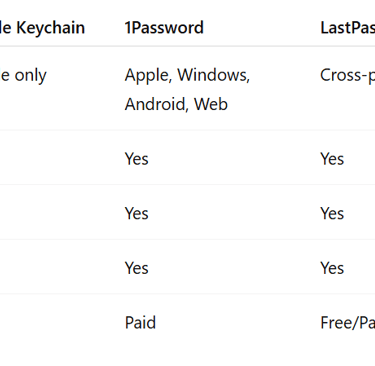
Apple Keychain vs Other Password Managers
When comparing Apple Keychain to popular password managers like 1Password, LastPass, and Dashlane, here is main difference:
Frequently Asked Questions (FAQ)
Apple Keychain is perfect for Apple-exclusive users looking for a simple, free solution. However, if user need cross-platform compatibility, advanced sharing, or password vaults for teams, then services like 1Password or Dashlane may be a better fit.
Is Apple Keychain safe from hackers? Yes, Apple Keychain uses strong encryption and biometric security. However, if Apple ID or device passcode is weak, user may still be vulnerable.
Can Apple see my passwords? No. Apple uses end-to-end encryption and zero-knowledge protocols, meaning even Apple cannot decrypt user's Keychain data.
What happens if I forget my Apple ID? If user forget Apple ID credentials and lose all trusted devices, user may permanently lose access to user Keychain data. Setting up Apple’s account recovery process in advance is recommended.
Does Apple Keychain work on Windows or Android? No. Apple Keychain is tightly integrated into the Apple ecosystem and does not officially support Windows, Android, or third-party browsers.
Final Verdict: Should You Trust Apple Keychain?
If user is fully immersed in the Apple ecosystem, Apple Keychain is a highly secure, convenient, and cost-effective password manager. It offers:
Industry-standard encryption
Seamless syncing across Apple devices
Biometric protection and 2FA
However, Apple Keychain may not suit user if:
He/She need to share passwords with others.
He/She use non-Apple devices.
He/She want more advanced password management features.
